INDUSTRIAL SECURITY MANAGEMENT PART 2
WHAT IS PHYSICAL SECURITY
PHYSICAL SECURITY is the protection of people, property, and physical assets from actions and events that could cause damage or loss. The most common forms of physical security are structures and man having the following purpose:
- deter potential intruders (e.g. warning signs, security lighting, and perimeter markings);
- detect intrusions and monitor/record intruders (e.g. intruder alarms and CCTV systems); and
- trigger appropriate incident responses (e.g. by security guards and police).
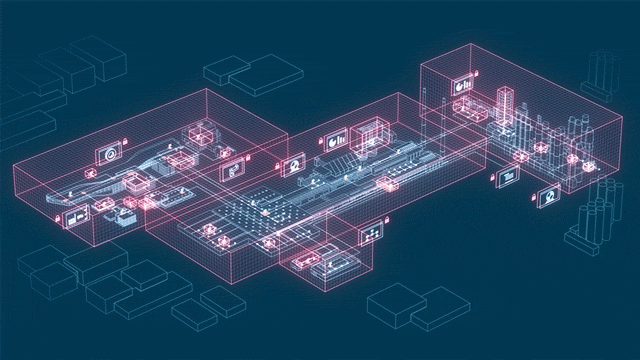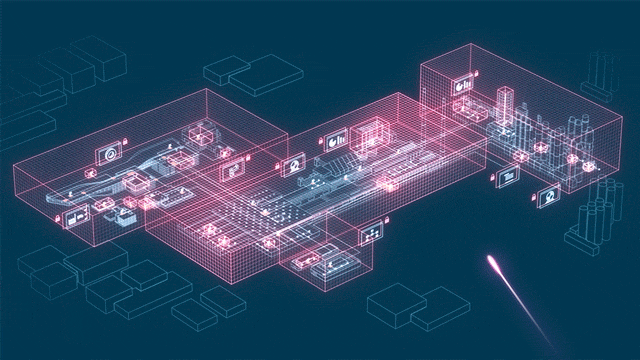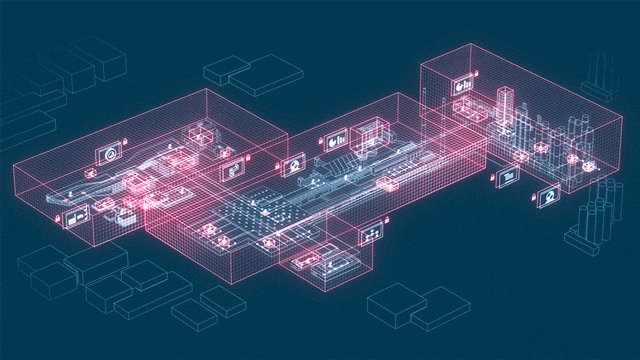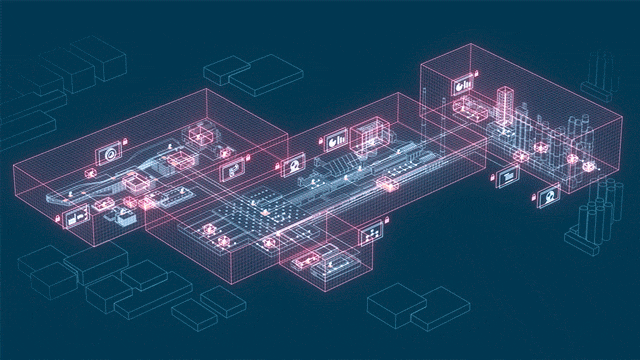
It is up to security designers, architects, and analysts to balance security controls against risks, taking into account the costs of specifying, developing, testing, implementing, using, managing, monitoring, and maintaining the controls, along with broader issues such as aesthetics, human rights, health and safety, and societal norms or conventions. Physical access security measures that are appropriate for a high-security prison or a military site may be inappropriate in an office, a home, or a vehicle, although the PRINCIPLES ARE SIMILAR, to instituting SAFETY & SECURITY.
The recent development of policing philosophy introduces Crime Prevention Through Environmental Design (CPTED) whose primary feature is about security, in criminology, this is more known as ENVIRONMENTAL CRIMINOLOGY. Though often overlooked in favor of cybersecurity, physical security is equally important.

THE NEED FOR SECURITY: Because Of the Factors that Bring About Insecure Condition
- Threats - positive inimical acts.
- Hazards - passive inimical conditions.
- Vulnerability - degree of exposure against intrusion, attack, or injury.
COMPONENTS OF PHYSICAL SECURITY
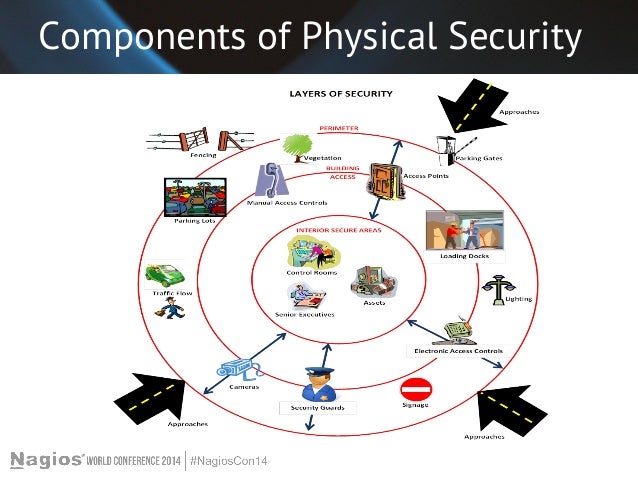
- Perimeter Barriers (1st Line of Defense)
- Building Exteriors (2nd Line of Defense)
- Interior Controls (3rd Line of Defense)
What are the GENERAL TYPES of physical barriers?
- Natural such as mountains, rivers, seas, and terrain.
- Man-made such as structural construction like fences, walls, floors, roofs, grills, etc.
PURPOSE OF BARRIERS
- Outline the perimeter of the area to be protected
- Create a physical and psychological deterrent to unauthorized entry
- Delay intrusion, thus facilitating apprehension of intruders
- Assist in more efficient and economical employment of guards
- Facilitate and improve the control of pedestrian and vehicular traffic
TYPES OF BARRIERS
Natural Barriers - refers to natural terrain features that delay or make the entry or access of intruder difficult. Examples: rivers, cliffs, ravines, etc.

Structural Barriers - refers to barriers or features constructed by man that tend to deny access or delay intrusion. Examples: walls, fences, roofing’s, ceilings, etc.

Human Barriers - refers to guards, office and shop workers who stand between the intruder and the matter being protected.

Animal Barriers - refers to canine or dogs trained to guard duties such as German Shepherds, Doberman, etc.

Energy Barriers - refers to the electrical or electronic devices used to enhance security in addition to the guard system. Examples: protective lighting and anti-intrusion alarm system

THE PERIMETER BARRIERS
It refers to the medium which defines the physical limits of an installation or area and restricts or impedes access thereto
It is a system of protection designed to restrict or impede access to restricted areas by unauthorized persons.

TYPE OF PERIMETER BARRIERS:
- Wire Fences
- Building Walls
- Bodies of Water

Main Purpose of Perimeter Barrier: To deny or impede access or exit of an unauthorized person.
The best example of perimeter barrier placed in an installation – FENCE
FENCE is an independent structure usually existing in a vertical plane, designed to control physical and/or visual access between outside areas.
TYPES OF FENCES
- Solid Fence
- Full View Fence
THE SOLID FENCE
SOLID FENCE is a fence constructed out of opaque materials in such a way that visual access through the fence structure is impossible.

Advantages of Solid Fence:
- It denies observation and viewing of the installation from outside.
- It denies intruder the opportunity to become familiar with the personnel, activities, and the time schedules and movement of guards within the installation.
Disadvantages of Solid Fence:
- It prevents the security guard from observing the area around the installation;
- It creates a shadow that may be used by the intruder as cover and concealment
THE FULL VIEW FENCE
FULL VIEW FENCE is a fence constructed in such a way that a visual access through the fence is possible. Barbed wire, cyclone wire (chain link), concertina, or decorative grills are examples of Full View Fence.

Advantages of Full View Fence:
- It permits 24-hour observation by roving and stationary security guards;
- It does not create shadows for possible cover and concealment
Disadvantages of Full View Fence:
- It allows visual access/observation to the installation by outsiders/intruders;
- It allows intruder to become familiar with the movement and time schedule of security personnel
SOME SPECIFICATIONS OF FULL VIEW FENCE
- At least 7 feet (8 feet including top guard)
- Vertical Clearance at the Bottom. No more than 2 inches
- Wooden Fence Post. Minimum horizontal dimension
- Fence Post. Should be Concrete
- Top Guard. 45-degree angle. Upward and outward
- Chain Link. Not more than 3 inches in diameter
THE PROTECTIVE LIGHTING
Security lighting provides a level of illumination to clearly identify persons or objects and creates a psychological deterrent to criminal activity in the area being protected.

Protective lighting should enable security personnel to observe activities at an installation without disclosing their presence. Adequate lighting for all approaches to an installation discourages attempted unauthorized entry and reveals persons in the area.
However, don't solely rely on lighting. You should use it with other measures, such as fixed security posts or patrols, fences, and alarms. Your goal is to place glaring lights in the eyes of the intruder and relatively little light on security patrol routes.
THE SECOND LINE OF DEFENSE
The second line of defense is the independent control function that oversees risk and monitors the first-line-of-defense controls. It can challenge the effectiveness of controls and management of risk across the organization.

Building Exteriors - 2nd line of defense
- Walls and roofing
- Doors and ceilings
- Windows & fire escapes
THE THIRD LINE OF DEFENSE
This high level of independence is not available in the second line of defense. An internal audit of the security system provides assurance on the effectiveness of governance, risk management, and internal controls, including the manner in which the first and second lines of defense achieve risk management and control objectives.
A broad range of objectives, including efficiency and effectiveness of operations; safeguarding of assets; reliability and integrity of reporting processes; and compliance with laws, regulations, policies, procedures, and contracts.
All elements of the risk management and internal control framework, which includes: internal control environment; all elements of an organization’s risk management framework (i.e., risk identification, risk assessment, and response); information and communication; and monitoring. Below are features of the 3RD LINE OF DEFENSE.
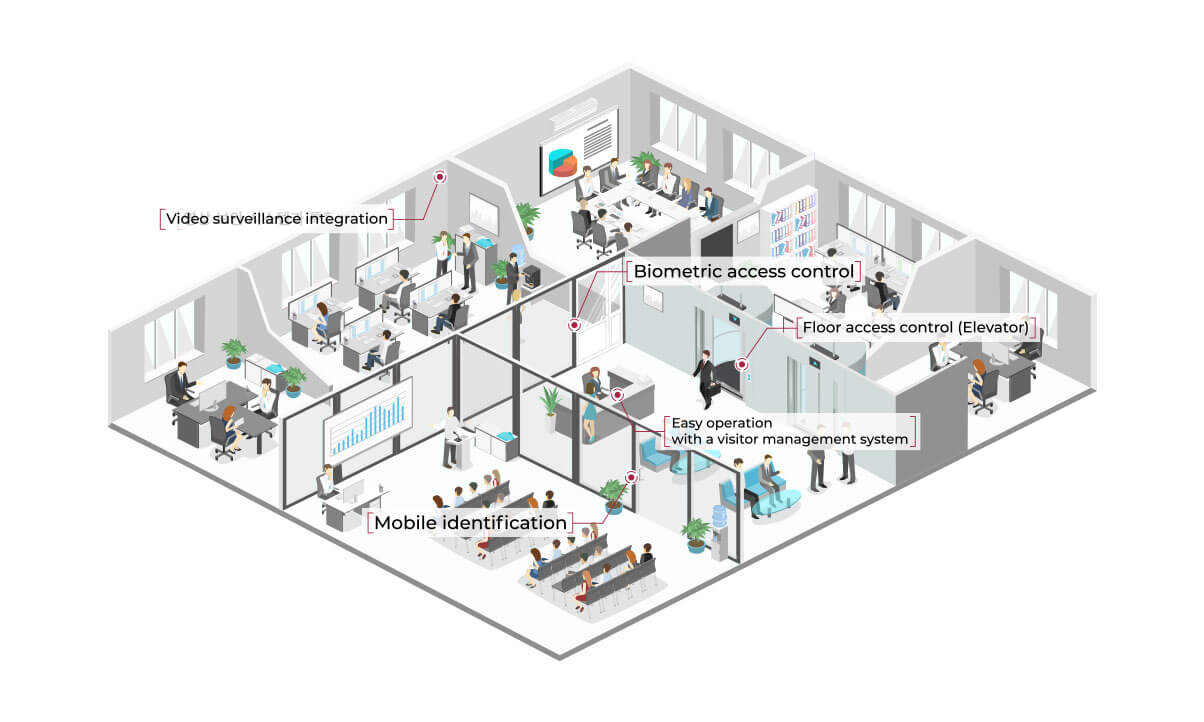
INTERIOR CONTROL- 3rd line of Defense
- Guard and Guard System
- Restricted Areas
- ID System and Access Control
- Entry/Exit Control (visitors, clients, suppliers)
- Vehicle Identification and Control
- Communication System
- Protective Alarm and Emergency System
- Emergency Plans
- CCTV, & Combined Electronic, Biometric, and Energy Barriers
- Key Management and Control
SUMMING up, below is the total security system expected for a safe environment whether governmental or industrial establishments.
GOING BACK TO THE FIRST LINE OF DEFENSE: Specifications for perimeter barrier (chainlink fence)
Specifications for Chain-link Fences
- Must be constructed of 7 feet material excluding top guard;
- Must be 9 gauge or heavier;
- Mesh opening must not be larger than 2 inches per side;
- Should be twisted and barbed salvage at top and bottom;
- Must be accurately fastened to rigid metal or reinforced concrete;
- Must reach within 2 inches of hard ground or paving
- On soft ground must reach below surface deep enough to compensate for shifting soil or sand.
Specification Regarding the Use of Barbed Wire
- Standard barbed-wire is twisted, double-strand, 12 gauge wire, with four points barbs spaced on equal distance apart.
- Barbed wire fencing should not be less than 7 feet high excluding the top guard.
- Barbed wire fencing must be firmly affixed to post more than 6 feet apart.
- The distance between strands will not exceed 6 inches and midway between parts.

PERIMETER BARRIER OPENING
- Gates and doors
- Sidewalk elevators
- Utility openings
- Clear zones

(Above is an example of a common opening and entrance to the protected establishment.)
A CLEAR ZONE is an unobstructed area which, should be maintained on both sides of the perimeter barrier.
SPECIFICATION ON CLEAR ZONE

- A clear zone of 20 feet or more should exist between the perimeter barriers and exterior structures, parking areas, and natural or man-made features.
- A clear zone of 50 feet or more should exist between the perimeter barriers and structures within the protected areas except when a building wall constitutes part of the perimeter barriers.
OTHER ADDITIONAL PROTECTIVE MEASURES OTHER THAN PHYSICAL AND PERIMETER BARRIERS
(1) TOP GUARD - it is an additional overhang of barbed wire placed on vertical perimeter fences facing upward and outward with a 45-degree angle with 3 to 4 strands of barbed wires spaced 6 inches apart.

(2) GUARD CONTROL STATION - located at the main entrance.
(3) TOWERS - guardhouse located above the perimeter barriers.

(4) Barrier Maintenance.
(5) PROTECTION IN-DEPTH - barrier after barrier.

(6) SIGNS AND NOTICES - these are control signs

SECURITY LIGHTING TECHNIQUES: (See also Protective Lighting)
Using protective lighting is a practical, cost-effective way to add a layer of security to your overall security strategy. Protective lighting delivers increased visibility for risk scenarios as well as the optimal visibility for security functions like video surveillance and guard duties.
- Security lighting should enable the guard to observe clearly the activities around and inside the premises within his jurisdiction.
- High contrast between intruder and background should be provided.
- Lighting the boundaries and approaches.
- The effective lighting system should:
- Deter or discourage attempts to enter the premises;
- Make detection more likely if entry is attempted;

TYPES OF SECURITY LIGHTING
(1) STATIONARY LUMINARY – continuous lighting either:
-
- glare projection
- controlled lighting

(2) STANDBY LIGHTING – similar to lighting but is turned on manually or automatically when there is suspicion of entry.

(3) MOVABLE LIGHTING – consist or manually operated movable searchlight which may be either lighted during darkness or only as needed.

(4) EMERGENCY LIGHTING – may duplicate the 3 systems in whole or in part, and is used during power failure or emergencies.

TYPES OF LIGHT LAMPS
- Incandescent Lamps (Fluorescent)
- Gaseous Lamps - also known as discharge lamps such as;
- Mercury - vapor lamps - blue-green in color.
- Sodium - (high & low pressure) vapor lamps - yellow light.
- Quartz Lamps - very bright light.
- LED (light-emitting diode)


(Standard lamp post or street light are common examples of mercury lamp)
PURPOSE OF INTRUSION ALARM SYSTEMS
- To economize
- To substitute in place of other security measures
- To supplement by providing additional controls
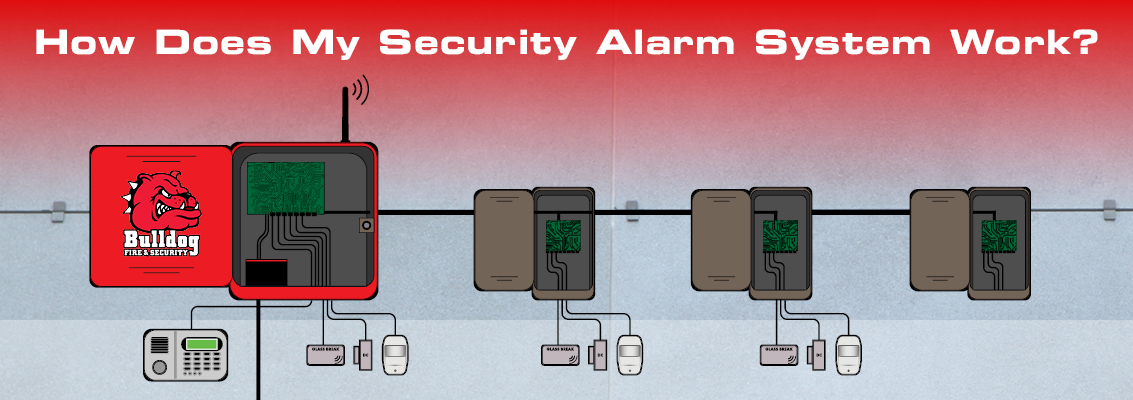
BASIC PRINCIPLES OF OPERATION OF INTRUSION DETECTION SYSTEM
- Breaking an electrical circuit
- Interrupting a light beam
- Detecting sound
- Detecting vibration
- Detecting a change in capacitance due to penetration of an electrostatic field.

(An example of anti-intrusion alarm system technology)
TYPES OF PROTECTIVE ALARM/ALARM DETECTION SYSTEMS
- LOCAL ALARM SYSTEM – this system consists of rigging up a visual or audible alarm near the object to be protected. In case of alarm, response will be made by the local guards and other personnel within sight or hearing.
- AUXILIARY SYSTEM – one in which the installation system owned is a direct extension of the police and fire alarm system.
- CENTRAL STATION SYSTEM – in this system, alarms are transmitted to a central station outside the installation from which appropriate action is taken, such as notifying the local police and fire department.
- PROPRIETARY SYSTEM – it is similar to the central station system, except it is owned by and located on the installation.

(Alarm system and technology: Camera identification equipped and auto-activation (voice activation, temperature activation, etc.) in case of disorder without manual manipulation)
COMMUNICATION SYSTEM IN SECURITY
- Local telephone exchange
- Commercial telephone service
- Inter-communication
- Two-way radios for security
- Security supervising system
- Paging and recall system
- Bull-horns or megaphones
- Amplifier or loud speaker systems
PASS and BADGE is issued by security for personnel to be admitted to the installation (entry and access control)
PROTECTIVE LOCKS AND KEYS CONTROL
FOUR GENERAL GROUPS OF KEY LOCKS
- Warded Lock – a lock that had been developed in the middle ages.
- Lever Tumbler Lock – lock used in safe deposit boxes and mailboxes.
- Disc Tumbler Lock – also known as wafer tumbler lock.
- Pin Tumbler Lock – the most widely used lock

COMBINATION LOCK is a lock that requires manipulation of parts according to a predetermined combination code of numbers or letters.
PADLOCK is used to secure two objects like a lock in the same relative position.
MASTER KEYING is when a lock operates on a master key plus an individual or change key. A MASTER KEY therefore can open every lock within a system (or building) and can be used when an independent key is LOST.
PASS KEY is a key used to operate an inexpensive lock by moving it in the keyhole until it catches the locking belt and unlocks mechanism. Some dictionaries considered pass key as a master key, but specifically, it is not. It is more known as INDEPENDENT KEY which operates only on a certain lock.
PICK LOCK. A picklock is a tool that can be used to open a lock without a key and normally used by thieves or burglars. There were countries that criminalize the possession of picklock.
TYPES OF FIRE ALARM SYSTEM

- Smoke Detectors - detect the presence of smoke.
- Ionization Detectors - detect particles created during the early stage of fire.
- Sprinkler Water- flow Detector - for an automatic sprinkler system.
TYPES OF AUTOMATIC SPRINKLER SYSTEM
- Wet Pipe System - water held in pipes.
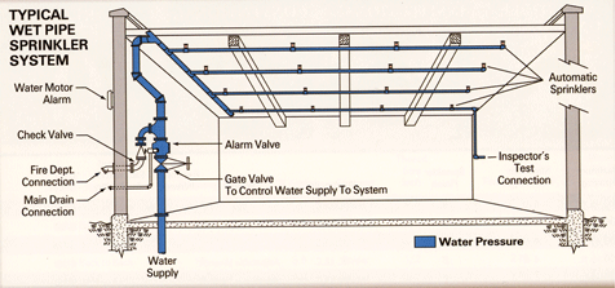
(Above is an example of a layout for a wet pipe sprinkler system)
- Dry Pipe System - when the sprinkler head is ruptured, a pressurized air escapes and water rushes into the pipes.

(Above is an example of a layout for a dry pipe sprinkler system)
- Deluge System - dry pipe installation except that it is designed to direct water flow in a chosen direction
(Above is an example of a layout for a deluge sprinkler system)
STORAGE SECURITY OF RECORDS
TYPES OF BUSINESS RECORDS
- Class I - Vital records (records that are irreplaceable)
- Class II - Important records (loss will involve considerable expense and cause labor)
- Class III - Useful records (loss will cause inconvenience but readily replaced)
- Class IV - non-essential records (daily files)
CATEGORY OR TYPES OF STORAGE CONTAINERS
- Class 1 - Commercial records safes designed for fire protection.
- Class 2 - Commercial money safes designed for robbery burglary protection.
- Class 3 - Security cabinets designed to meet specifications for safeguarding classified materials.

VAULTS is an enlarged safe. VAULTS are classified according to fire resistivity such as two, three, or four hours. The considerations for the construction of vaults are:
- Location
- Vault Utilities
- Structural Foundation
- Doors
GUARD SYSTEM is the strategic placement and combination of human, animal, and energy barriers between the intruder and the matter to be protected.
2 Basic Techniques of Guard Employment: Advantages: Disadvantages: Advantages: Disadvantages: (An Act Governing the Organization & Management of Private Security Agencies, Company Guard Forces and Government Security Forces) Disqualifications for LICENSE to operate and exercise Security Profession: (Sec. 4) What is SAGSD? RA 5487 defines SAGSD to the current PNP Civil Security Group Security Agency and Guard Supervision Division or any other PNP Office that may be designated later as the primary office for supervision and implementation of RA 5487. Who may organize and maintain a Private Security Agency and Private Detective Agency? (Rule IV, Part 1, Section 1) What are the basic requirements of an operator or manager of an agency? (Rule IV, Part 1, Section 2) What is the minimum number of licensed private security personnel can be employed by a private security agency? 200 What is the minimum number of licensed private security personnel that can be employed by a company guard force or private detective agency? 30 What is the maximum number of private security personnel that a private security agency/company guard forces/private detective agency can be employed? 1000 How long is the duration of License To Operate (LTO) private security agency? 2 years. All temporary LTOs upon expiration are automatically canceled. What are the Basic Requirements of private security personnel? (Rule V, Section 2) What are the Qualifications of a Private Security Guards? (Rule V, Section 3) What are the Qualifications for Security Officer? (Rule V, Section 4) What are the Qualifications for Security Consultants? (Rule V, Section 5) What are the Qualifications for a Private Detective? (Rule V, Section 6) Who are exempted from Basic Pre-licensing Training? (Rule V, Section 7) What are the types of licenses stipulated under RA 5487? How is government security personnel licensed? (Rule V, Section 10) No person shall be licensed as a Government Security personnel unless he possesses the qualifications as prescribed in Section 3, 4, and 5 of rule V, provided he submits an appointment order coming from the Civil Service Commission. (You can read more about RA 5487: see link below) Functions of Human Guard System

TYPES OF GUARD FORCE SYSTEM

Proprietary Guards
Contract Guards

SIGNIFICANT INFORMATION RELATED TO R.A. 5487
ARE YOU READY TO TAKE THE TEST?
You can proceed now to the examination and input your complete name for validation (kindly complete your name please)
GOOD LUCK
This quiz is for logged in users only.



660 thoughts on “Industrial Security Mngt Part 2”